Since this months’ issue revolves around security I thought it a wise idea to discuss some tips and tricks that are security related. To that end I hope to explore some of the common useful options for ssh. First we will examine TCP port redirection using the ssh client, which can generally only be accomplished via root level privileges.
Since we are not going to alter the sshd_config to allow ALL users on the system the redirection privilege I am assuming that you have a working system where you hold the proverbial keys to the kingdom. If I am mistaken then perhaps you should download an ISO of your favorite BSD or even a live DVD like RoFreesbie so that you can play along.
First I would like to discuss why one might consider creating a ssh TCP tunnel. Let us decide that you are visiting a new client for the first time and have not had a chance to setup your normal exclusionary firewall rules, and further that this client’s network is one you do not entirely trust as of yet. However you need to access data on the intranet back at your office. This could be some files, or your client database, or even you jabber server. While there are numerous methods available to facilitate this sort of action we are going to tunnel some TCP via an ssh connection.
There for in this example let’s expect that you need to access your MySql database securely form outside of your home network. As previously mentioned we will assume that you have root level access on the source system, which is most likely you personal laptop.
Reading the ssh man page you will note the -L [bind_address:]port:host:hostport which may seem cryptic at first however we will deconstruct the command one parameter at a time. First consideration is the bind_address, this is only an issue if your system has multiple address and you wish to specify which one to use for the outgoing connection. This is the only optional parameter in the statement one that we can safely ignore. The port refers to the port on your local machine at this end of the tunnel, in other words the port that you wish to map the service on target machine to. The host refers to the address of the host on the remote side of the tunnel. This host may the the target machine itself or another machine available on the same LAN as the the target. Finally the hostport is the TCP port that you wish to connect to.
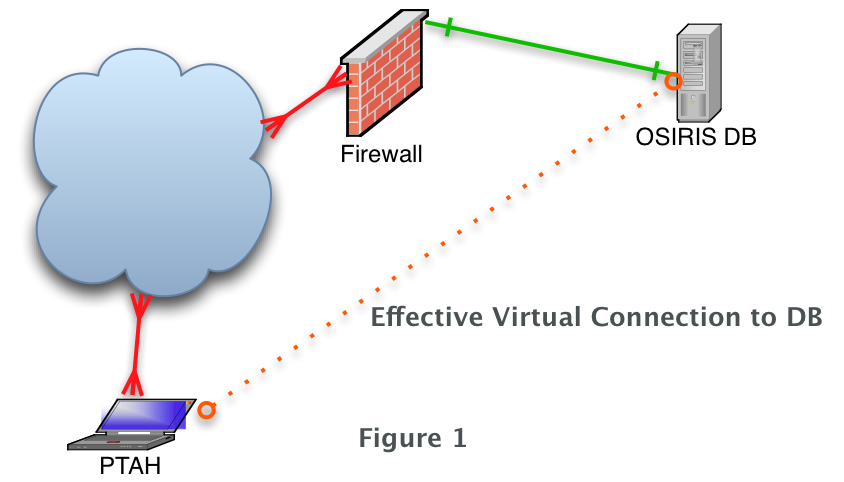
In this exercise we will be connecting to our database server OSIRIS.olivent.com via another server PTAH.olivent.com. These machines have appropriate DNS entries so as to ensure that I can always connect to them by their proper name. From here after I’ll simplify things by only referring to them by their short names in all capital letters for clarity.
In the following example I will be opening a connection to the target machine ptah as the user sysmgr.
# ssh -N -f -L 4406:OSIRIS:3306 sysmgr@PTAH
As you can see that did not really do very much, now on my local machine I can direct my MySql client to connect as follows.
PTAH> mysql -h 120.0.0.1 -P 4406 -u dbadmin -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 26621
Server version: 5.0.67-log Source distribution
Type ‘help;’ or ‘\h’ for help. Type ‘\c’ to clear the buffer.
mysql>
To summarize what thus far we have successfully established an ssh tunnel to our target and told ssh that no CLI access is needed as well as to send the connection to the background. We were then able to connect to the MySql database pretty much as we would if we were sitting at the console of the server in question, by simply adding the appropriate host and port switches as demonstrated above. Refer to Figure 1 below for more detail. Refer to Figure 1 below for more detail.
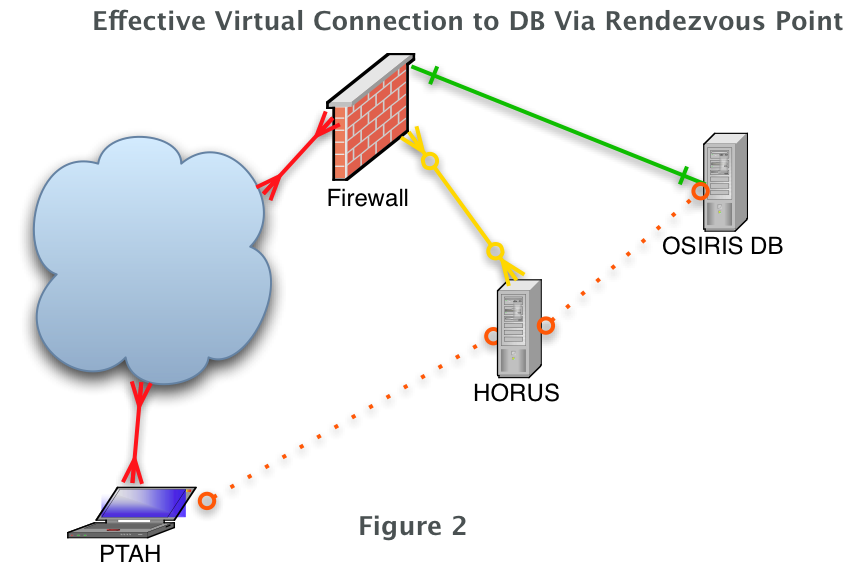
Suppose however you manage a site and need to allow a vendor to access and troubleshoot a server but do not wish to grant this vendor full access to the entire network. How do you allow them to complete their work without being able to peruse your entire network? The answer is called a rendezvous point.
In order to facilitate rendezvous point you need three machines. The server, the client, and the way station. The server and client are fairly obvious but the way station is the meeting point in this case we will call that machine HORUS. HORUS lives on the DMZ and exists solely for the purpose of facilitating these sorts of connections. It’s firewall rule prohibit more external access excluding ssh of course.
In the following example first the database server OSIRIS is connected to the way station HORUS.
OSIRIS# ssh -N -f -R 4406:127.0.0.1:3306 sysmgr@HORUS
Then the vendor on PTAH connects to the way station as shown.
PTAH# ssh -N -f -L 5506:127.0.0.1:4406 sysmgr@HORUS
Finally the vendor opens their database utility connecting to the newly bound 5506 port on their local IP address.
PTAH> mysql -h 120.0.0.1 -P 5506 -u dbadmin -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 26626
Server version: 5.0.67-log Source distribution
Type ‘help;’ or ‘\h’ for help. Type ‘\c’ to clear the buffer.
mysql>
As you can see from the demonstration above the vendor is able to access the database and perform what ever maintenance is required within the limitations of their database utilities. To further secure this method one could issue a ssh key pair so that no passwords need to be exchanged in the first place. What is nice about this later step is that once the maintenance has been completed simply revoke the vendor’s key at the way point HORUS and terminate the tunnel from OSIRIS to HORUS.
In addition if the vendor’s account is compromised in anyway the only access will be granted to HORUS which knows absolutely nothing about your internal network. In fact other than being a basic BSD server it should know nothing about databases, DNS, mail or anything other how to connect to the internet. Obviously it adds a layer of complexity to the whole process, as well as yet another server to maintain, but in the end is you have a large installation of vendor supported equipment and loath the idea of letting them run amuck about your network it certainly is viable option.
Leave a Reply